
Visit our website. Stay updated with the latest news by following us on X. Builders, developers, and curious minds are welcome to join our Telegram group to chat with the team.
Proofcast is a products suite that democratizes access to cryptographic proofs backed by Trusted Execution Environments (TEE) with the first “proving-as-a-service” solution based on trusted hardware.
What are TEEs?
TEEs are isolated execution environments within the main processor, where both code and data are protected at the hardware level. The secure enclave ensures:
- Confidentiality: code and data within the TEE are isolated and cannot be accessed by any unauthorized components, including the operating system and hypervisor.
- Integrity: the code and data within the TEE are shielded from tampering, even by privileged software or physical attacks on the hardware.
- Hardware Attestation: TEEs support cryptographic attestation, enabling the generation of verifiable proofs that the code executed inside the TEE is authentic and has not been altered.
Why it matters?
The transition of blockchain infrastructure to a modular design—such as the separation of settlement and execution in Ethereum—has created a demand for coprocessors. These are designed to offload on-chain computation to specialized layers optimized for efficiency and cost, enabling data-intensive and computation-heavy applications.
Cryptographic proofs, particularly succinct proofs, have become the standard to ensure the security, integrity, and confidentiality of these off-chain computations
The limit of zk-proofs & the future of TEEs
zkVMs (like SP1 or Risc0) accelerated the adoption of zk-proofs with a revolution in abstraction and user experience, eliminating the need to design custom circuits and reducing overhead for developers.
We believe the same will happen with Trusted Execution Environments.
The next generation of on-chain applications will rely on the co-processing power provided by TEEs. Use cases like decentralized physical infrastructure networks (dePIN), decentralized AI (dAI), and on-chain gaming cannot be fully supported by zk technology alone.
However, many teams today face the challenge of building trusted hardware solutions from the ground up. They must develop custom applications and code, all while navigating fragmentation between various TEEs (like Intel SGX, AWS Nitro) and diverse proving networks.
The future of TEEs: “proving-as-a-service”
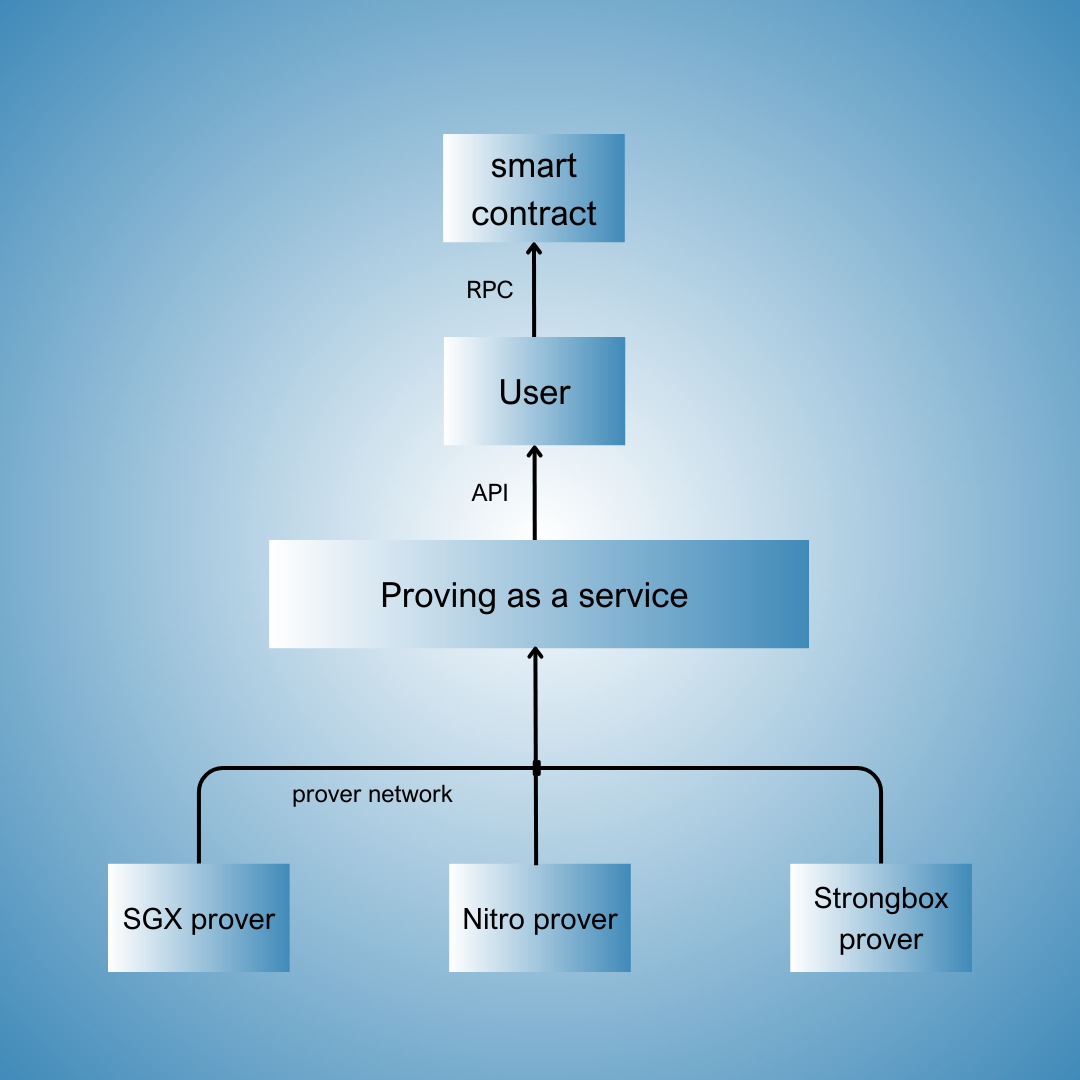
Proofcast wants to become the “proving-as-a-service” standard for TEEs.
We bet on giving developers better accessibility and UX by leveraging:
- Abstraction: working with TEEs should be as simple as pressing a button and running your code;
- Selection: our stack aims at supporting all types of devices (Intel, AWS, Android, etc.);
- Customization: no lock-in network or standalone product, but a suite tailored to specific needs.
Our go-to-market is a suite of products that currently range from the first general-purpose TEE-VM, to event attestator (cross-chain) and light clients.
 Tee-VM
Tee-VM
Overview
Proofcast TEE-VM is a RISC-V runtime environment inside a Trusted Execution Environment (TEE). It enables builders to write Rust code allowing the execution of guest programs inside a RISC-V VM to provide proof of execution. The necessary I/O primitives are provided to facilitate communication with the VM, with access to a public API.
Proofcast TEE-VM targets fast and ready-to-use TEE devices, enabling builders to write coprocessors for production use today while preserving low gas impact for on-chain validation. By initially working with AWS Nitro, Proofcast TEE-VM will support all the relevant ready-to-use TEE devices in the future (Strongbox, SGX).
Developers in the space of dAI, dePIN & on-chain gaming can focus on their core code without setups or maintenance overhead of trusted hardware. They choose Proofcast TEE-VM as a plug&play proving solutions with the best performance / security tradeoff.
Components
Proofcast TEE-VM includes the following components:
- Rust Crate: Equipped with the necessary I/O primitives to allow communication to and from the RISC-V VM.
- Command-Line Interface (CLI): Serves as the user's gateway to the runtime environment, enabling the execution of user code.
- TEE Runtime Environment: Responsible for executing user code, returning the output of computations, and providing proof that the computations were executed as intended. While we provide the execution layer, users deploy their own supported TEE. Initially, we support the StrongBox TEE, with plans to support additional TEEs in the future.
Public Good
Proofcast TEE-VM is a public good: it is freely accessible and operates on a permissionless basis. The Rust crate, CLI, and runtime environment will all be published as open-source repositories. This allows the community to freely access the codebase, fostering collaboration and innovation.
 Event Attestator
Event Attestator
Overview
The Event Attestator is part of Proofcast's suite of proving services. In conjunction with the TEE Wrapper, it can be used to get proof that an arbitrary event has taken place in a configured blockchain. Along with proof of inclusion, the validity of the block containing the target event is also checked, for a number of supported blockchains. Once an event proof has been output from the Event Attestator, it is possible to verify it on chain with a solidity smart contract.
Drawing from extensive experience in the field of cross-chain asset bridging, Proofcast empowers the Event Attestator with a large library of supported blockchain on which events can be defined, detected and validated. Compared to up-and-coming zero knowledge proof (ZKp) based verification, thanks to the trusted execution environment (TEE) backed TEE Wrapper, both off-chain prooving and on-chain verification are inexpensive, giving the Event Attestator a short and medium term competitive advantage.
Purpose and Use Cases
While with Proofcast's TEE-VM it is possible to prove the execution of arbitrary code, the Event Attestator focuses more closely on the task of proving events. It can be run by anyone with a supported TEE enabled device, by simply configuring selected blockchain details and event information.
Event proving is necessary for a number of cross-chain operations, such as:
- Asset bridging
- DAO synchronization
- Cross-chain swaps
Proofcast's Event attestator can be used on its own or in conjunction with other proving services such as through LayerZero Omnichain and Hashi's SafeJunction.
Architecture
The Event Attestator currently supports Android Strongbox's TEE; more platforms are being integrated.
The project is structured like follows:
common/: low level library providing all the code for block validation and proof generation for each supported blockchainapps/: lightweight JSONRPC HTTP server abstracting the interaction to the TEE contained into the device
The system at a glance:
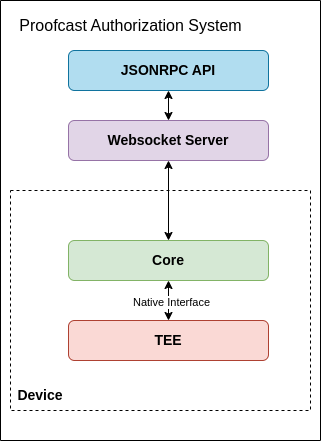
- The JSONRPC api allows the end user to send commands to the device
- These commands are then sent through the websocket channel to which the device is connects on startup
- The core library deserialize each message coming from the websocket channel and process them accordingly
Setup for EVM chains
-
Copy the configuration sample from
sample-config.tomlfile in the common folder and configure it to your needs, in particular be careful to fill up the[networks.chainName]section with theendpointsproperty. -
For each configured chain, set the
eventsarray where each element is in the following form:
["<contract-address>","<topic>"]
- Build the app
cargo build --release --bin jsonrpc-app
- Run
./jsonrpc-app -c <config.toml>
- Set up the TEE Wrapper in order to connect the app to the device.
When everything is connected you can manually process a block of interest on the
configured chain with the process method, as in the following call:
curl \
-X POST \
-H 'Content-Type: application/json' \
-d '{"jsonrpc":"2.0","id":1,"method":"process","params":["bsc", "38745426", "false", "true"]}' \
http://127.0.0.1:3030/v1/rpc
The output will include all the signatures for the configured events in the
signed_events array:
{
"id": 1,
"jsonrpc": "2.0",
"result": {
"latest_block_num": 38745426,
"network_id": {
"chain_id": 56,
"disambiguator": 0,
"protocol_id": "Ethereum",
"version": "V1"
},
"signed_events": [
{
"block_hash": "0x1535c8e9ab42918c2df9d05ba18a816dafc2e3eba45fffc334d2890a2ebcc0bf",
"encoded_event": "0100016162636465656666200000000000000000000000000000000000000000000000000000000000000000005af3107a4000",
"event_id": "abcdeeff",
"log": {
"address": "0xf5e11df1ebcf78b6b6d26e04ff19cd786a1e81dc",
"data": [],
"topics": [
"0xddf252ad1be2c89b69c2b068fc378daa952ba7f163c4a11628f55a4df523b3ef",
"0x000000000000000000000000b0116a2cab9774e9d75834dcce64f99fd75a8579",
"0x0000000000000000000000000000000000000000000000000000000000000000"
]
},
"public_key": "03572d2b94ea3918ecd104cdd84a07efc1f9cbc1f11bbd02a6418179894d0d2fc6",
"signature": "02a893f433fcd688558931a1ab8041c8384ac710550e8ab22c705233c68bd12c38c085405ca6d2c5ea3db8d1b6b84d49f46f070239dcc06aa3c4ec78ea72cb0f01",
"version": "V1"
}
],
"timestamp": 1716302631
}
}
 Introduction
Introduction
The low level nature of Trusted Execution Environments prompts the use of an abstraction layer in order to facilitate the interaction for the end user. This project aims to create this layer by creating a websocket connection to the host to whom the device is connected and will interpret all the commands sent by the host as low level calls. Through this application it is therefore possible to run a rust program inside an Android TEE using a websocket connection to communicate to the outside.
Architecture
The architecture consists into different layers:
- React app: very thin layer which makes the developing on the device easier
- App android: where the websocket client is started continuously polling for the host connection
- Java Native Interface (JNI): the command coming from the host is serialized in bytes and sent to a lower level call implemented in Rust
- Core: the actual rust code which is being wrapped interacting with the underlying TEE. This is dynamically loaded when the Android app starts and where the commands are actually executed. Once the result is available it get serialized again and returned to the apps and forwarded to the host through the websocket connection.
Setup
Requirements
An android device with TEE hardware
- JAVA SDK 11 installed
- Android SDK installed (v33)
- Android NDK installed (v25)
Optional
- Android Studio
Steps
- Link the Rust library project into the rust folder (be sure it compiles when running
cargo build --release): - Create a
local.propertiesfile into theandroid/folder with the path to the android SDK and NDK:
sdk.dir=/opt/android-sdk
ndk.dir=/opt/android-sdk/ndk/25.2.9519653
- Plug the device and run
npm run plugDevice
- Run the reactive-app
npx react-native start
Press a in order to compile and install the app on the device.
- Open websocket ports between the android device and the computer:
- Now the app is looking for a websocket connection to the port
3000on localhost.
This page is a work in progress.
The BitcoinZ Light Client from the Proofcast suite offers an accessible, less resource-intensive way to interact with the Bitcoin blockchain. As interchain operability grows, light clients will be crucial for verifying chain status, such as verifying Bitcoin state on an EVM-compatible chain.
Key Features
- Zero-Knowledge Proof: Utilizes sp1 and risc0 zero-knowledge proofs.
- SP1 zkVM: Implemented in Rust.
- RISC0: Supports CPU and GPU runs.
Usage
To integrate and test the BitcoinZ Light Client, follow the instructions provided in the GitHub README.
This page is a work in progress.
The BitcoinT is the TEE Bitcoin light client developed by Proofcast.